Previously, Blockonomi has highlighted how crucial understanding malware is within the cryptocurrency domain, and sadly, this peril remains. A fresh strain of malware is now targeting cryptocurrency transactions, adopting a method that defies usual expectations.

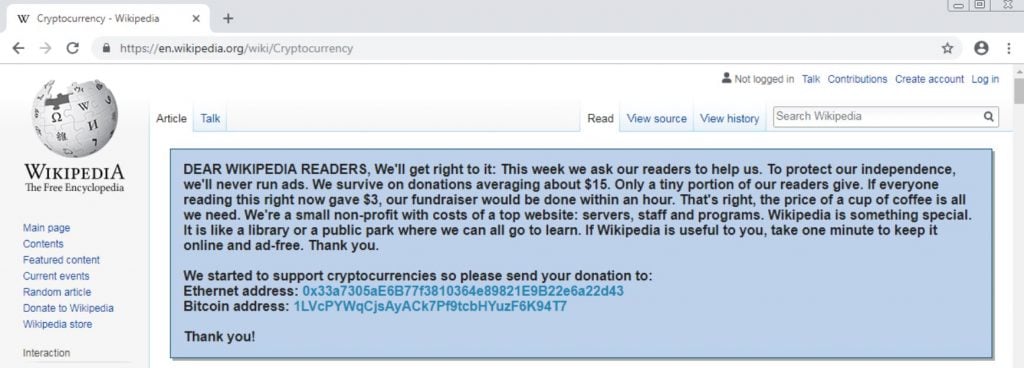
This malware utilizes artificial intelligence (AI), and once it infiltrates your device, it lurks silently until the cybercriminals behind it can access your login credentials. However, its malevolent activity is not immediate. The malicious code patiently waits until the unsuspecting user navigates to a Wikipedia entry. Often, a banner appears, urging visitors to make a nominal contribution to support Wikipedia.
When you click on this, you're directed to a section indicating Wikipedia's acceptance of cryptocurrency donations, displaying Bitcoin and Ethereum wallet addresses on-screen. Unfortunately, those addresses aren’t directed to Wikipedia’s coffers…
This malware executes its deceit by substituting the legitimate donation addresses with the hackers’ own. Consequently, the unfortunate donor ends up contributing funds not to Wikipedia but to the hackers responsible for injecting the malware.
The Threat Exists on Larger Levels
To make matters even scarier, this problem isn’t confined to just Wikipedia. A cybersecurity insider reveals:
“It’s more than just Wikipedia that's at risk of displaying phony crypto addresses. The malware is engineered to substitute addresses wherever it can across a multitude of websites.”
For example, this malware has demonstrated the capacity to modify Google search results and alter displayed ads on sites users visit. Typically, Google charges a hefty fee for top ad placement, yet these hackers manage to bypass typical protocols, enticing unwitting individuals.
Things Are Getting Rough Out There
It’s quite alarming, showcasing the sophisticated nature utilized by spammers and cyber miscreants to amass wealth, particularly highlighting the elaborate schemes involved. This type of attack likely demands intricate coding, although, to be honest, it’s not the first instance of crypto-centric malware appearing on the scene.
Historically, the crypto sector has grappled with malware manifested as crypto-jacking schemes, where malicious software commandeers a user’s computer to mine cryptocurrency covertly. Most commonly, Monero—famed for its privacy—is targeted. Additionally, such mining processes often lead to substantial energy expenses for the victim.
Among the more recent malicious strains is include Smoke Loader , which has been elevated by cybersecurity company Check Point as one of the top ten most hazardous malware forms today. The notorious Smoke Loader deploys other malware forms such as Trojans, TrickBot, and Panda Banker. Allegedly, Smoke Loader downloads these onto infected systems, multiplying the victim’s woes.
The Issue Intensifies
Check Point’s threat intelligence and research division head, Maya Horowitz, stated:
“The sudden popularity of Smoke Loader underscores a growing trend in the Global Threat Index for harmful, versatile malware, with the top ten categories split evenly between crypto miners and malware that uses diverse methods for spreading numerous threats.”
Other significant threats include Coinhive, still widely deployed today. Coinhive exploits Monero mining and has been discovered on major platforms like Google apps.
On a more positive note, there's hope on the horizon as several analysts suggest hackers and malware perpetrators might soon back off from crypto loot as cryptocurrency valuations decrease.





