The CryptoNote Reference Implementation serves as a crucial protocol layer powering multiple renowned decentralized cryptocurrencies that prioritize privacy. open-source The technology is crafted to offer innovative privacy features based on high-level cryptography, promoting decentralization and resisting censorship.
The CryptoNote Cryptocurrencies Leveraging CryptoNote Technology

Background on CryptoNote
The founding document pinpoints Bitcoin's flexibility and privacy shortfalls, focusing on transaction linkability and traceability while promoting Bitcoin's original one-CPU-one-vote concept proposed by Satoshi Nakamoto. It introduces a robust set of new characteristics for decentralized networks, termed as CryptoNote Technology. original whitepaper CryptoNote Technology is predicated on achieving two key privacy measures needed for genuine anonymity in transactions: second version Untraceability ensures that all potential senders of a transaction appear equally probable, masking the origin.
Unlinkability ensures that it's impossible to definitively link any two transactions to the same recipient. proposed Since its inception, the original proposal has been refined with numerous updates, maintaining its innovative edge while adhering to its foundational values. A registry of protocol specifications can be found on the CryptoNote website, where its main features are highlighted.
CryptoNote Technology
CryptoNote facilitates untraceable payments through ring signatures. Originating from a concept by David Chaum and E. van Heyst that further evolved in a subsequent paper, ring signatures intermingle numerous public keys to hide the transaction signer's identity while ensuring transaction validity. Today, several CryptoNote currencies have adopted (Ring CTs) to build upon the initial traceable ring signatures.
- Untraceability
- Unlinkability
Unlinkable transactions are achieved with the use of one-time keys. While a ring signature allows for visible transactions to a public key, CryptoNote mitigates this by generating one-time keys for each transaction using the recipient's public key. An enhanced system allows for a secure shared secret between parties, enabling the transaction initiator to hash the receiver's public key with personal data to create a unique key for the transaction. Subsequently, only the recipient can derive the private aspect, allowing them to unlock the funds upon completing the transaction.
Achieving a double-spend proof while obscuring transaction data poses challenges. CryptoNote ingeniously uses key images to verify this without sacrificing anonymity. Key images allow for unique trace markers without revealing the signer's identity. In scenarios like Alice attempting multiple transactions using the same key, a key image identifies potential double-spending without isolating her identity. Transactions with matching key images faced outright rejection by the network.
Blockchain analysis has evolved as a prominent area for research and innovation, presenting methods to assess on-chain activities. Innovations have revealed ways to peel back pseudonymity in networks like Bitcoin. However, the use of unique one-time keys in each CryptoNote transaction prevents any correlation between input and output through public addresses. standards To encapsulate, sender identities are hidden using ring signatures, the transaction amounts are masked by Ring CTs in currencies like Monero, and the recipient's privacy is shielded with one-time address mechanisms.
- Untraceable Payments
- Unlinkable Transactions
- Double-Spending Proof
- Blockchain Analysis Resistance
- Egalitarian Proof of Work
- Adaptive Parameters
CryptoNote's focus on an egalitarian proof of work arises due to Bitcoin's mining centralization risks with ASICs. When the CryptoNote document was conceived, Bitcoin allowed CPU mining, which has since waned due to specialized hardware. Given Bitmain's IPO indicating it controls 37.1 percent of Bitcoin's mining capacity, CryptoNote's foresight against ASIC domination is apt, even if a 51 percent attack seems far-fetched. group signature Mining centralization also impacts off-chain governance, adding complexity. Concentrated mining power slows network upgrades but supports Bitcoin's cautious evolution. CryptoNote notes that Bitcoin’s SHA-256 mining algorithm inadvertently favors costly custom devices (like ASICs) over general CPUs. It highlights the 80/20 rule common within Bitcoin's ecosystem, prompting a shift to a memory-bound approach for work proofing to distribute mining influence more evenly. Traceable Ring Signature An exemplified mining algorithm found within CryptoNight was later rolled out, proving adept at resisting ASIC mining, allowing only CPU and GPU operations. However, with constant advancement in chip technology, maintaining such resistance remains tricky, prompting Monero to constantly adjust protocols to sustain its ASIC-resistant stance. Ring Confidential Transactions A notable aspect of CryptoNote is its emphasis on adaptive parameters. Hardcoded limits, like block size and difficulty, present challenges as seen in Bitcoin’s block size debates that led to the Bitcoin Cash fork. CryptoNote counters these with dynamic adjustments per block relative to specific conditions.
For instance, Monero’s moving block size caps at 2 * M100, where 'M' is the median of the last 100 blocks, effectively alleviating blockchain bloating and negating transaction size constraints. Furthermore, Monero recalibrates difficulty after every block using a 720-block data range, omitting 20 percent outliers, aligning with the CryptoNote guide for difficulty determination. Diffie-Hellman Key Exchange Overall, the range of features within CryptoNote Technology harnesses exceptional mathematical principles. Structured as an open-protocol, it establishes a foundation for emerging cryptocurrency markets committed to decentralization and privacy.
Today, numerous cryptocurrencies adopt the CryptoNote Reference Implementation technology, invariably incorporating the core technology tailored for each currency's distinct objectives.
CryptoNoteCoin embodies the unique CryptoNote Technology application. Its genesis block is redesigned biennially with zero commercial leverage. Features include the capability to fork the CryptoNoteCoin protocol and initiate your own cryptocurrency based on CryptoNote. companies You may explore by downloading the CryptoNoteCoin blockchain, engaging in transactions, and mining experiments.
Bytecoin, the pioneering CryptoNote currency from 2012, emerged closely with the CryptoNote team. Celebrated today, it integrates CryptoNight mining and typical CryptoNote privacy attributes like ring signatures and a gradually decreasing emission rate. Prominently, Bytecoin prioritizes rapid, fee-less transactions, aiming to serve enterprises globally with safe, confidential, and swift payments.
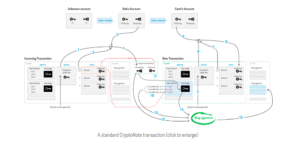
Image Credit – CryptoNote Website
Monero stands as the most renowned privacy-focused currency nowadays. Its supportive decentralized network actively contributes to its growth and network benefits, making Monero a formidable force for confidential transactions. prospectus A Comprehensive Beginner's Introduction to CryptoNote Technology
CryptoNote Technology is notable for its groundbreaking privacy measures, leveraging sophisticated cryptographic techniques, promoting decentralization, and ensuring resistance to censorship. Pareto principle A Comprehensive Guide for Beginners on CryptoNote Technology
The CryptoNight The foundational CryptoNote Reference Implementation is a protocol situated at the application layer, underpinning various renowned cryptocurrencies known for their focus on privacy and decentralization. Bytecoin and subsequently optimized for Monero This technology distinguishes itself by offering state-of-the-art privacy aspects, grounded in advanced cryptography, a fair commitment to decentralization, and an inherent deterrence to censorship. fork Well-Known Cryptocurrencies Implementing CryptoNote Principles

Read: How to Mine Monero
CryptoNote's backstory is as enigmatic as Bitcoin's. It surfaced in 2012, first appearing on Tor, credited to an anonymous creator named Nicolas Van Saberhagen. The mysterious authorship continued even after a whitepaper, under the same pseudonym, emerged later.
The seminal paper addresses Bitcoin's limitations regarding privacy and transaction traceability, underscoring weaknesses in transaction linkability and the 'one-CPU-one-vote' philosophy originally put forth by Satoshi Nakamoto. By using 'we,' the document introduces a fresh set of pioneering attributes for decentralized cryptocurrencies, called CryptoNote Technology.
CryptoNote Technology is constructed to ensure two crucial features needed for complete anonymity in digital payment networks: open-source Untraceability signifies that for each incoming transaction, all potential senders are equally likely to be identified as the origin.
CryptoNote has a similarly enigmatic background to Bitcoin. Emerging onto the scene in 2012 via Tor, it was authored under the pseudonym Nicolas Van Saberhagen, whose true identity remains undiscovered.
Unlinkability represents the ability to prevent proving two outgoing transactions were sent to the same recipient.
CryptoNoteCoin
Since its initial proposal, the technology has seen several enhancements to stay at the forefront while preserving its core tenets. The CryptoNote website maintains an updated protocol specification, and the Reference Implementation spotlights features such as:
- CryptoNight Mining Algorithm
- 30 Second Block Time
- 18.4 Million Coin Supply
- Full Re-Emission Every 2 Months
CryptoNote provides some excellent resources Untraceable payments are achieved in CryptoNote through the adoption of ring signatures, a concept which stems from David Chaum and E. van Heyst, and later evolved into CryptoNote's variant using ring signatures. By incorporating numerous public keys, they obscure the actual transaction signer while permitting valid transaction verification. Ring CTs are a refined version in practice in several CryptoNote coins today. wallet Unlinkable transactions are realized by producing one-time keys. Although all incoming transactions to a single address can be observed with a ring signature, CryptoNote averts this by auto-generating unique keys from the recipient's public key per transaction. This alongside an optimized version of cryptographic security ensures a shared secret for transaction participants. Thus, only the recipient can derive the private key, enabling them to access the funds once it's locked into the blockchain.
Bytecoin

Bytecoin Ensuring a double-spend proof within an oblivious environment poses certain complexities. CryptoNote tactically utilizes 'key images' to preclude double-spending in an opaque ledger, offering anonymity to the signer. Identifying such attempts without revealing identity is feasible since a key image is retained in network records, hindering any transaction linked to a public key or signer. Transactions with redundant key images are automatically refused by the network.
Monero

Monero With Blockchain Analysis, there has been increasing interest in investigating on-chain behaviors due to advancements in both blockchain and cryptocurrency networks, revealing ways to deanonymize users. However, CryptoNote thwarts efforts to trace transactions via unique one-time keys, blocking linkage through public addresses. open-source In conclusion, ring signatures obscure sender identity, transacted amounts are anonymized through Ring CTs (as seen in Monero), and one-time addresses maintain recipient anonymity.
The Kovri Project CryptoNote's focus on egalitarian proof-of-work is a response to the concentration risks in Bitcoin arising from ASIC mining tech. During CryptoNote's inception, CPU mining was still feasible in Bitcoin, but it was becoming obsolete with the emergence of tailored mining equipment. With entities like Bitmain purportedly influencing 37.1% of Bitcoin's mining hash, CryptoNote’s proactive stance on ASIC control is validated by concerns of potential 51% attacks. Bulletproofs , a zero-knowledge proof technology.
Conclusion
Mining centralization additionally impacts off-chain governance, complicating network updates while sometimes benefiting Bitcoin's cautious development strategy. CryptoNote critiques Bitcoin’s SHA-256 algorithm for not adequately addressing ASICs' dominance over standard CPUs. CryptoNote evokes an analogy (pertinent to Bitcoin’s scenario), where a minority of participants govern the majority vote share, advocating for a memory-intensive algorithm that balances proof-of-work power distribution. CryptoNote Foundation An example of such an algorithm is the mining process used in certain CryptoNote coins, safeguarding against ASIC mining and favoring CPU and GPU mining. Although maintaining ASIC-resistance is challenging due to advancing hardware, Monero recently adapted its protocol to keep its defenses intact.






2Comments
There are numerous cryptocurrencies incorporating the CryptoNote Reference Implementation today. While they adopt the technology in varying degrees, they typically feature bespoke optimizations suited to their specific aims.
CryptoNoteCoin serves as the Reference Implementation of CryptoNote Technology, bearing no commercial worth, with its Genesis block refreshing every two months. Technological features showcase: