Cryptocurrencies like Bitcoin often implement privacy mechanisms both at the level of the blockchain and their communication network layer. With public blockchains, each transaction is permanently recorded, making it crucial to obscure transaction details and anonymize the identities of parties involved. both Coins with a strong focus on privacy, such as Monero and Zcoin, build in anonymity features at the blockchain level to ensure transactions remain untraceable. However, the network layer, responsible for peer-to-peer communications, is equally essential in safeguarding interactions throughout a cryptocurrency network. Network privacy features in cryptocurrencies often undergo prolonged development and can introduce certain drawbacks.
Originally suggested in 2017, Dandelion aimed to bolster privacy within Bitcoin's P2P networking. However, it emerged that its initial iteration relied on overly optimistic assumptions about potential threats, which could eventually compromise anonymity. Monero and Zcoin In May of this year, a refined version named Dandelion++ was proposed. This iteration addresses the earlier concerns and has already garnered positive feedback from Bitcoin's development teams, signaling its potential inclusion in an upcoming Bitcoin Core release. Ring CTs and zero-knowledge proofs Dandelion++ is a streamlined and efficient solution ensuring network layer anonymity. It fixes the theoretical assumptions of the original proposal and stands out by setting different goals and analytical metrics compared to other anonymity protocols focused on broadcast communications. Tor and I2P Understanding Dandelion++ necessitates a look at how Bitcoin transaction broadcasts work. When a user sends a transaction, it's initially shared with its node's direct peers. This message then cascades, with each node further relaying it to its peers, thus spreading across the network in what's known as the gossip protocol, allowing rapid dissemination.
The Dandelion protocol Bitcoin now counteracts the risk of exposing a user's IP address through a broadcast method called diffusion, where nodes share transactions with staggered, independent delays to adjacent nodes. However, diffusion alone does not offer complete anonymity protection. faults While a Bitcoin transaction message doesn't disclose an IP address, it’s still possible for third parties to trace it back to the origin. By using tactics like supernodes or analyzing the data flow, they can pinpoint the initial node and its address. Dandelion++ aims to break this traceability by altering how transactions are spread before they're broadcast in the wider network.

The initial Dandelion proposal didn't hold up to practical scrutiny, largely due to its reliance on three overly simplistic assumptions. Dandelion++ The first assumption was that each node would only originate a single transaction, among others.
What is Dandelion++?
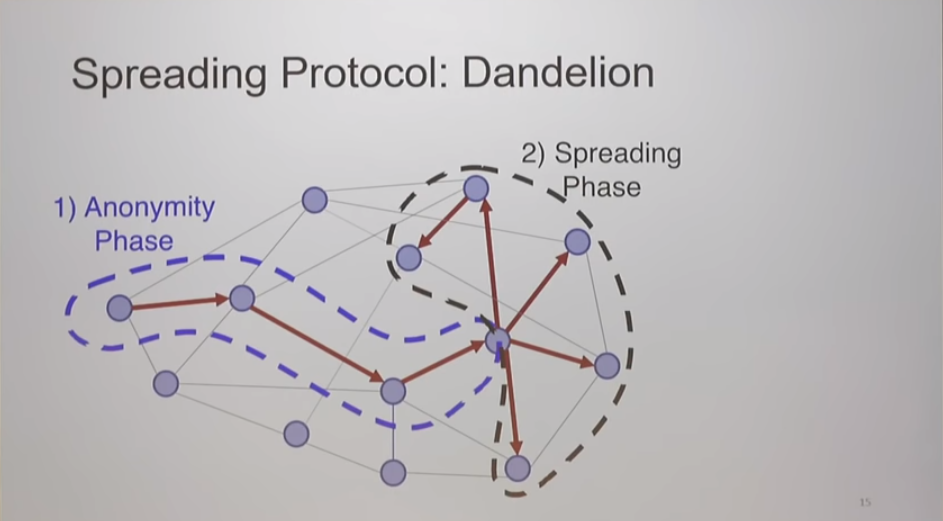
These presumptions were impractical, spurring the development of Dandelion++. The protocol works through two stages: the stem and fluff phases.
During the stem phase, transactions are cautiously relayed through a carefully chosen privacy graph, reducing the risk of linking back to the sender's IP. The message hops from one node to another in a random sequence until it is eventually spread network-wide using the diffusion approach.
In the fluff phase, once a node uses diffusion to broadcast the transaction, it proliferates to many nodes, making it challenging to trace it back to its origin. This diffusion makes it difficult for observers to pinpoint the originating node, obscuring the sender's identity akin to a ring signature concept. recently Giulia Fanti’s presentation in Lisbon provides a humorous analogy for the Dandelion protocol using a high school gossip scenario.
Kathy: \"Pssst, I have a huge crush on Nuwa... Don't tell anyone!\" control enough nodes George: \"OMG, Kathy just told me she has a massive crush on Nuwa. I’m only telling you, don’t spread it!\" paper Alice: \"You won’t believe what I heard from George about Kathy’s crush on Nuwa! Your secret’s safe with me, but don’t tell anyone else!\"
Blabbermouth Betty: \"Juicy news alert...I heard from a reliable source that Kathy is crushing on Nuwa! Spread the word, it's big news!\"
- All nodes obey the protocol
- The original Dandelion protocol faltered primarily due to its oversights about adversaries' capabilities and their information. Dandelion++ strategically modifies the protocol's structure and message transmission methods to improve its resilience.
- All Bitcoin nodes run Dandelion
These refinements escalate the complexity for anyone attempting to compromise user anonymity. Dandelion++ expands on the data adversaries must gather to successfully de-anonymize users.
- Stem Phase
- Fluff Phase
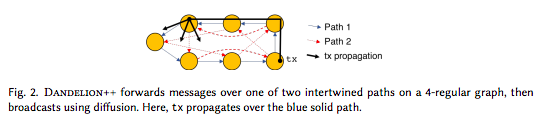
A key difference in Dandelion++ is during the stem phase, where transaction messages traverse intertwined connections called cables before spreading to the network. These paths can be split, yet the selection of nodes for transaction forwarding remains local.
Unlike broader systems like Tor, which require global network awareness, Dandelion++ operates with a local focus and thus poses fewer integration challenges.
Both Dandelion iterations function in asynchronous cycles, dictated by each node’s internal timer. Dandelion++ optimizes this process with four primary components.
The Zcoin blog An anonymity graph now utilizes a 4-regular graph rather than a linear approach for enhanced privacy. Node selection remains independent of their outbound connections’ agreement to the protocol.
*STEM PHASE*
- Transaction forwarding (own) refers to nodes forwarding their own transactions along the same network edge, unlike the single-transaction assumption in Dandelion.
- During transaction forwarding (relay), nodes decide whether to relay a transaction or distribute it network-wide, with nodes categorized as either a diffuser or relay.
- A fail-safe mechanism tracks transactions during the stem phase, ensuring they transition to the fluff phase. If not, the node itself disperses the transaction.
*BEGIN FLUFF PHASE*
- Algorithm nuances at each stage elevate the difficulty of correlating IP addresses with transaction behaviors. Dandelion++ thoroughly explores potential attacks such as graph-learning, intersection, and construction attacks, and proves its defenses through theoretical analysis and simulation.
Dandelion++ maintains low network latency and its feasibility has already been confirmed on Bitcoin’s mainnet, cementing its role in anonymity protection. However, ISP and AS-level adversaries remain outside its protective scope, as they could leverage routing attacks.
When compared to other network anonymity options like Tor, Dandelion++ holds distinct advantages.
Tor is a renowned privacy-centric network that employs onion routing to safeguard users’ locations and IP.
Integrating Tor with cryptocurrencies presents significant challenges, evident in Monero’s efforts to incorporate a Tor-like I2P system, taking over four years and still ongoing. Many blockchain developers lack the resources or expertise required for such integration.
Understanding The Dandelion Protocol: A Beginner's Overview
- Anonymity Graph
- Transaction Forwarding (own)
- Transaction Forwarding (relay)
- Fail-Safe Mechanism
Introduced in 2017, the Dandelion protocol was designed to enhance privacy within Bitcoin's P2P network by offering an anonymity solution.
A Comprehensive Guide for Beginners: The Dandelion Protocol Uncovered
Cryptocurrencies such as Bitcoin focus on privacy both on the blockchain and within the network layers. With public blockchains keeping a permanent log of digital exchanges, privacy solutions aim to conceal transaction details and shield the identity of transaction parties. pseudorandom Digital assets emphasizing privacy typically include features at the blockchain level, making tracking nearly impossible. Yet, privacy in P2P network communication is equally crucial across a blockchain's digital ecosystem. Monero and Zcoin, for example, have implemented network-level privacy strategies, though these came with extended development timelines and other challenges.
Initially suggested in 2017, this network layer solution sought to bolster Bitcoin's P2P network privacy. The early design included certain vulnerabilities due to hypothetical threats.
An upgraded version of Dandelion, known as Dandelion++, was presented in May this past year. It tackles the initial protocol's issues and has been met with approval by Bitcoin’s developers. There's a good chance it'll feature in an upcoming update of Bitcoin Core.
Dandelion++ is a straightforward network layer anonymity option, providing robust anonymity and simple integration into existing cryptocurrency frameworks. By rectifying the overly optimistic assumptions of the original Dandelion and differing in user goals and analytical metrics from traditional anonymity broadcasting protocols, Dandelion++ shows promise.
Comparing Dandelion++ and Tor
To grasp how Dandelion++ functions, we need to consider Bitcoin's transaction broadcasting method and the initial Dandelion approach. In Bitcoin, a node broadcasting a transaction sends the message to its peer nodes. This ripple effect, known as Bitcoin's gossip protocol, disseminates the transaction swiftly throughout the network. Tor Bitcoin has moved to a diffusion method of broadcasting, where nodes propagate transactions at varying, exponential intervals to neighboring nodes, helping to obscure a user's IP address. Though effective, diffusion alone doesn't completely shield user anonymity.
By intercepting or using a supernode connected to many other nodes, third-party entities can potentially identify the transaction's originating IP, which isn't part of the Bitcoin transaction message. Tracking which nodes receive the transaction first lets them pinpoint the source. Research on Dandelion++ reveals how supernode studies were able to monitor transaction dissemination patterns, detailing how IP addresses could be pinpointed over time. Subsequent transactions can then be linked to those IP addresses, even when new public keys are used. Kovri Designed to mitigate such vulnerabilities, Dandelion struggled due to its reliance on theoretical assertions that faltered upon practical application. The original Dandelion made three main assumptions:
Every node generates only one transaction,
The same study These assumptions were impractical, leading Dandelion++ to address them. Initially, Dandelion functioned in two phases:
Conclusion
The 'stem phase' focuses on minimizing the chance of a transaction tracing back to its originating node's IP. Instead of broadcasting widely, a node uses a privacy graph to randomly send the transaction to one peer, following a specific algorithm. This continues from peer to peer until one node eventually broadcasts the message across the entire network using the diffusion strategy. privacy in Bitcoin .





