Serving as a backbone for blockchains, Merkle Trees are pivotal in facilitating the secure and efficient verification of expansive data structures.
Incorporating Merkle Trees into blockchain technology supports its scalability and fortifies its data integrity framework through a hash-driven system.
Understanding cryptographic hash functions is vital, as they form the foundation enabling Merkle Trees' functionality.
Summary Insight: Merkle Trees are built from cryptographic hashes, empowering systems like blockchains with robust data verification and efficient large-scale data mapping.
Quick Facts
| Key Points | Description |
|---|---|
| Cryptographic hash functions | Hash functions process inputs of varying sizes and generate a fixed-length hash, a notable element in Merkle Trees. |
| Merkle tree structure | A data structure in which each parent node's hash is derived from its child nodes, facilitating efficient large-scale data verification. |
| Root hash | The root hash at the top of a Merkle Tree acts like a digital fingerprint for the entire data set. |
| Merkle proofs | Verification of data's integrity and its position within the tree is possible with just the root hash, eliminating the need for access to the full data set. |
| Implementation in Bitcoin | Merkle Trees' transaction storage in blocks, with their root hash in the block header, enables SPV nodes to authenticate transactions. |
| Other blockchain implementations | Adopted in multiple blockchains like Ethereum, which utilizes advanced Merkle Patricia Trees for complex data structures. |
| Distributed systems | Merkle Trees empower version control systems such as Git and IPFS to streamline peer-sharing of verified data. |
Cryptographic Hash Functions
In essence, a hash function translates data of any arbitrary size into a fixed-length output. Through hashing, this output becomes a unique signature, or hash.
Various publicly accessible hashing algorithms cater to different needs, offering flexibility in data processing.
The hash produced is consistent in length and uniquely corresponds to the input data, providing a deterministic process.
Consider distinct input data sets: even minute changes result in markedly different hashes, highlighting the uniqueness of each hash.
This fundamental trait allows data to be distinctly 'fingerprinted'.
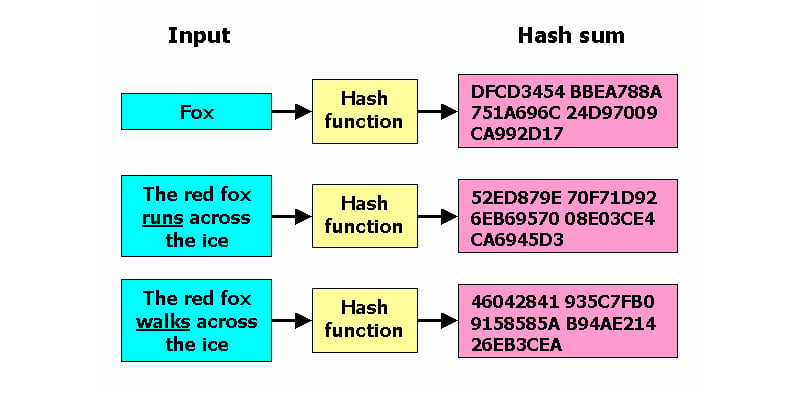
Cryptographic hash functionality exemplified through imagery. Wikipedia
With hash sums always of a predetermined length dictated by the algorithm, huge data volumes are swiftly identified by these outputs.
Utilizing fixed-length hashes for comprehensive data management translates to storage efficiency and streamlined data operations.
Within the realm of blockchain, hashing algorithms determine the blockchain's current state.
The blockchain's structure likens to linked lists, chaining data blocks through hash pointers, hence the moniker 'blockchain'.
Data blocks, interconnected via hash pointers that compile previous blocks' data, encapsulate the blockchain's comprehensive state.
For example, utilizing the SHA-256 algorithm, it yields a specific output hash like this:
b09a57d476ea01c7f91756adff1d560e579057ac99a28d3f30e259b30ecc9dc7
This particular hash mirrors the prior state of the blockchain, where the hashed prior state serves as input.
While hash functions on their own can replace Merkle Tree use, the efficiency drop and scalability issues make them suboptimal.
Merkle Trees introduce a simplified resolution to data integrity concerns, permitting seamless tree traversal via Merkle proofs.
Merkle Trees and Merkle Proofs
Ralph Merkle, who first patented these trees in 1979, devised a system where parents are the hash sum of their children's nodes.
Within the tree's lowest level, leaf nodes reside. A primary look at the widely known diagram clarifies the entire structure.
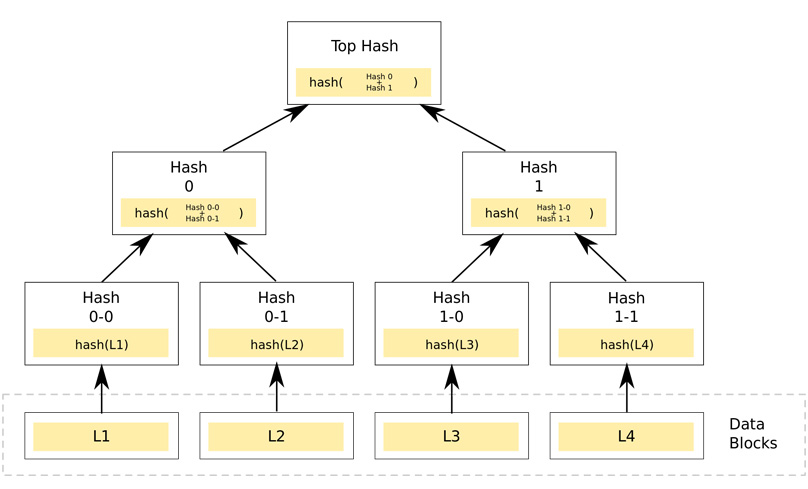
A simple depiction of a binary hash tree, encapsulated through imagery. Wikipedia
Key observation: non-leaf or 'branch' nodes are child hashes. For instance, Hash 0 links through its successors Hash 0-0 and Hash 0-1.
Presenting the Binary Merkle Tree, the most recognizable model. The pivotal root hash symbolizes the entire tree's hash.
This tree structure enables efficient data mapping with minimal checks, permitting straightforward change detection upon data nodes.
Merkle proofs advocate data verification through restricted hash checks against the known, reliable root hash.
Any database lookup can verify data position and integrity against a tree's publicly trusted root via Merkle proof.
Even with partial tree access, data integrity remains verifiable, one branch at a time, thanks to the root hash.
Remarkably, Merkle Trees enable authentication of extensive data sets, echoing smaller-scale data verification processes' simplicity.
By compartmentalizing vast data collections into manageable sections, verification thresholds are reduced despite enormity.
The root hash serves as a comprehensive fingerprint, representing any vast data collection or entire blockchain state. Bitcoin Next, we explore further systems' deployment of Merkle Trees.
Merkle Trees in Bitcoin
SHA-256, a pivotal cryptographic hash function employed by Bitcoin Of note in Merkle Trees' context, blocks cultivate and systematically diminish transactions per each block. Bitcoin is to store Connecting blockchain blocks through successive block hashes is foundational, exemplified by Bitcoin's transaction and header design.
Illustrating Merkle Trees' integral role within individual blocks.
- Block Version Number
- Previous Block Hash
- Timestamp
- Mining Difficulty Target
- Nonce
- Merkle Root Hash
The image below is from the Bitcoin whitepaper Miners incorporate transactions within blocks, hashing them into a Merkle Tree, reaching the root hash in the header.
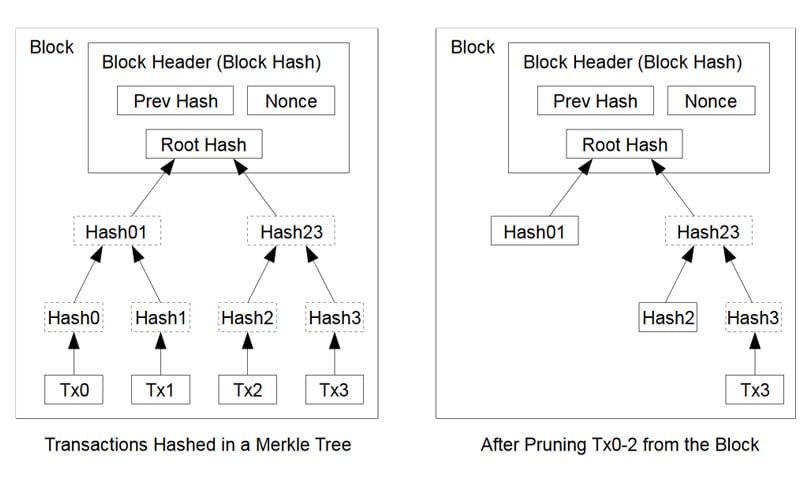
Notably, it's the infrastructure enabling Simple Payment Verification (SPV) nodes, facilitating lightweight clients needing only block headers.
SPV nodes query fellow peers, confirming the alignments of block headers with the longest chain, facilitated by Merkle proof.
Bitcoin harnesses Merkle Trees for blockchain pruning, conserving space by streamlining unessential tree branches for proof preservation.
While Bitcoin spotlighted Merkle Trees first, other blockchains adopt and evolve this structural approach.
Utilizing Merkle Trees Across Various Blockchain Platforms and Other Systems
Expanding beyond blockchains, Merkle Tree utilization spans a wide array of system applications.
Ethereum, another key player, employs a sophisticated Merkle Tree variant called the Merkle Patricia Tree, handling various data types.
Ethereum Ultimately, exploring deeper into Merkle Trees underscores their role in distributed systems like Git's. a platform Merkle Trees, a cornerstone of distributed versioning, especially in systems like Git, consolidate data management efficiently. here .
An Introduction to Merkle Trees: Navigating the Basics of This Key Blockchain Element IPFS Delve deeper into how Merkle Trees are pivotal to the core workings of blockchains, with a special look at their application in Bitcoin.
Conclusion
Merkle Trees play a crucial role in blockchains, ensuring they operate smoothly with verifiable immutability and secure transaction processing.
Understanding Merkle Trees: A Newcomer's Exploration into this Core Blockchain Element






4Comments
Very informative.
Thanks
Quick Insight: As structures of cryptographic hashes, Merkle trees ensure efficient integrity checks for substantial datasets, key to functioning systems like blockchains and distributed version control.
Wow, very well written – thank you!
good article but:
Diverse Applications of Merkle Trees across Blockchains and Other Systems
Hash functions convert varied size inputs into fixed length outputs, pivotal for the operation of Merkle trees.