NordVPN Positioned as a front-runner in the VPN industry, NordVPN boasts a commitment to providing absolute anonymity, unrestricted internet access, and top-tier security capabilities.
NordVPN portrays a VPN as a fortified conduit for online data traffic, ensuring protection against breaches and offering an added layer of security and confidentiality for users. With NordVPN, clients can surf the web assured of their private browsing. Additionally, NordVPN elaborates on how their offerings enable users to conceal their identity, ensuring digital privacy.

By masking your IP address, you evade surveillance and censorship, protecting your digital footprint. This practice also facilitates seamless streaming without bandwidth limitations. It allows for secure interactions with P2P networking or remote access from workplaces. NordVPN highlights that while proxies alter IP addresses, they fall short in concealing online activities, risking exposure of personal information.
Join us as we thoroughly explore NordVPN to see if it genuinely ranks among today's leading VPN selections.
NordVPN Quick Facts
| Category | Information |
|---|---|
| VPN Provider | NordVPN.com |
| Servers | Over 5,200 servers in 60 countries |
| Simultaneous Connections | 6 devices |
| Money Back Guarantee | 30 days |
| Logging Policy | Strict no-logs policy |
| Encryption | Military-grade AES-256 encryption |
| Protocols | IKEv2/IPsec and OpenVPN |
| Speed | Blazing-fast servers for negligible slowdown |
| Streaming | Streaming perfected with SmartPlay optimization |
| P2P Allowed | Yes, optimized P2P servers |
| Apps | Supporting Windows, Mac, iOS, Android, Linux, and proxies |
| Customer Support | 24/7 live chat and email |
| Pricing | Starts at $11.95/month ($6.99 with 1 year plan) |
History of NordVPN
NordVPN Their journey began in 2012 with four lifelong friends. Witnessing censorship and surveillance worldwide, they felt compelled to address these issues. They initiated research into countering these digital threats and established their initial VPN server, sharing the prototype with close circles. Encouraged by positive feedback, they widened their scope.
The moniker NordVPN draws inspiration from Nordic values of trustworthiness, ingenuity, and assurance. These principles reflect NordVPN's emphasis on customer autonomy. Currently, NordVPN caters to over 12 million users globally and receives accolades from prominent IT security experts. Their reputation as a dependable provider of security and privacy services is well-earned.
Number of Servers & Locations
The efficacy of a VPN service is largely influenced by the server count and distribution. A wide geographic spread of servers boosts reliability and performance, offering more IP address options. Recognizing this, NordVPN boasts an impressive quantity of over 5,200 servers across 60 nations, ensuring a server is always nearby. This vast array ensures each server handles lighter loads, enhancing speed.
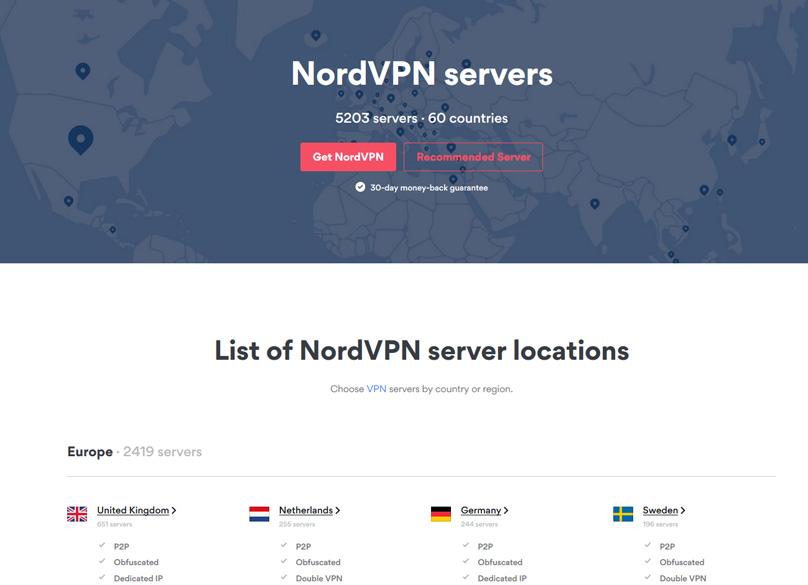
Access NordVPN’s comprehensive server list on their Server Location page. Servers are categorized by region and country, showcasing available features via checkmarks, such as Double VPN, dedicated IP, P2P, obfuscation, and Onion Over VPN.
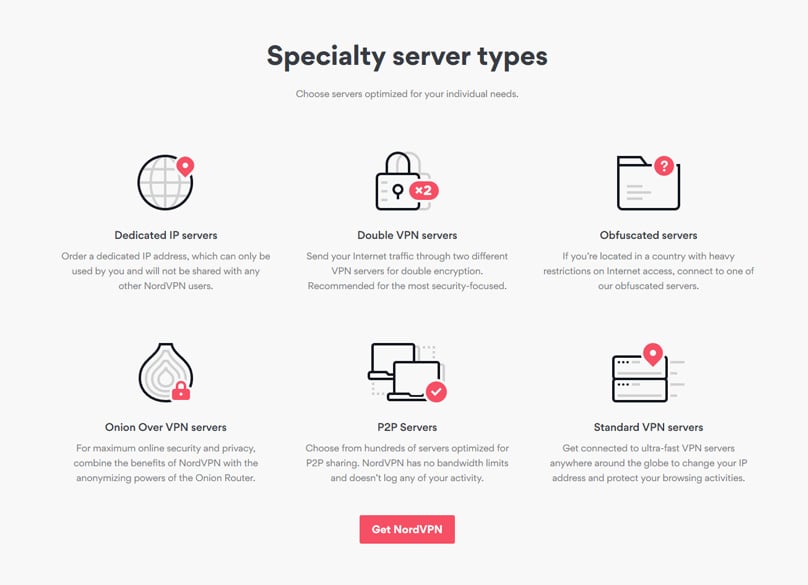
NordVPN's automated smart algorithm identifies the optimal server based on your specifics like location and load requirements. You'll observe specialty server types with distinct features for varying needs.
Dedicated IP servers assign you a unique IP address, free from shared use. Double VPN servers provide enhanced protection through their Double VPN settings. Similarly, Onion Over VPN servers deliver the Onion Over VPN service. For those facing strict internet controls, obfuscated servers offer a solution, while P2P servers are tweaked for peer sharing. Standard servers maintain impressive speeds while securing privacy.
When Should You Consider NordVPN’s Dedicated IPs?
Most NordVPN users don't require a dedicated IP, but certain situations make it crucial. It's beneficial for accessing business networks with added security by whitelisting your dedicated IP, ensuring exclusive use.
Dedicated IPs are also advantageous for online banking, preventing misleading signals that could alarm your bank into suspecting malicious activities when logging in from varied locations.
They also help avoid blacklisting risks associated with shared IPs, potentially caused by others misusing the IP. Continuous CAPTCHA challenges on popular shared IPs could become tiresome, so a dedicated IP might offer peace of mind.
Shared IPs, however, enhance online anonymity by blending your history with numerous users'. A personal static IP from NordVPN involves additional costs.
Does NordVPN Keep Logs?
Contrary to several VPN services, NordVPN adheres to a strict no-log policy, ensuring no record of client online actions exists. Because NordVPN doesn’t log data, they cannot share or be compelled to disclose any information.
For added assurance of personal data integrity and online privacy, NordVPN’s About Us page includes a Warrant Canary. This guarantee affirms NordVPN's full control over its infrastructure, with no breach or compelled data disclosure, nor any unwarranted system alterations.
Beneath this declaration, NordVPN makes three pivotal assertions upholding privacy, valid as of the site's viewing date. These confirm no receipt of gag orders, national security letters, nor government warrants. Ultimately, it reemphasizes NordVPN's unwavering no-log policy.
NordVPN’s Privacy
Emphasizing a stringent no-log approach, NordVPN vows not to track, collect, or divulge personal data. They only gather essential information vital for service provision, crucial since VPNs protect data from ISPs but could otherwise capture that data.
To further elucidate NordVPN's no-log stance, consider untracked logs. Connection logs show no record of server use, data volume, or connection particulars. Usage logs omit sites visited, files downloaded, or software used.
Though other VPNs assert no-log policies, they might still monitor connection logs, risking third-party identification from these records.
Alongside NordVPN's no-log assurance, they subjected their claims to an audit by one of the Big 4 firms, verifying the accuracy of their no-log declarations.
NordVPN strategically chose their base location to ensure maximum user confidentiality, free from U.S. and EU data retention mandates.
NordVPN’s knowledge about their clientele is restricted to email, payment details, and the last session’s timestamp, along with rudimentary customer service data and site usage. Beyond such essentials, user privacy remains intact.
Key Features of NordVPN
NordVPN's key offerings are designed to maintain digital safety, featuring aspects like double VPN, CyberSec, and high-grade encryption. Together, these protect against malware, block ads, and shield activities on public networks.
Further safeguarding features include steadfast no-log commitments, DNS leak defenses, Onion Over VPN, and an Automatic Kill Switch. Compatibility across all devices ensures secure usage anytime, anywhere.
With NordVPN, you explore the internet freely, unperturbed by bandwidth caps or censorship, thanks to an array of servers, SmartPlay, P2P support, and remarkable speed.
Eliminate Ads & Dangers with the CyberSec Function
NordVPN's CyberSec is cutting-edge tech designed to preempt access to dubious sites, shielding against cyber threats and obtrusive ads. By cross-referencing web addresses with blacklists, you’re safeguarded against malware or phishing.
CyberSec stops bots, ensuring malware-infected devices don’t partake in DDoS offensives by severing connections between botnets' command centers and devices. It also blocks autoplay video ads and pop-ups, speeding up load times and reducing nuisances.
NordVPN’s Double VPN
NordVPN’s Double VPN boosts online security by routing traffic through two VPN servers, encrypting and obscuring activities twice over, enhancing anonymity.
Once your online traffic reaches the distant VPN server, it remains safely encrypted. From there, it passes through an additional VPN server, adding an extra layer of security. The Double VPN ensures your information is wrapped in two layers of encryption, providing added protection against hackers.
The Double VPN feature enhances security by using both TCP and UDP protocols in the communication process. Notably, the second server holds no knowledge about you because the initial VPN server alters your original IP address. This approach delivers absolute privacy, ensuring your final internet destination remains unseen by prying eyes, merely indicating your VPN usage.
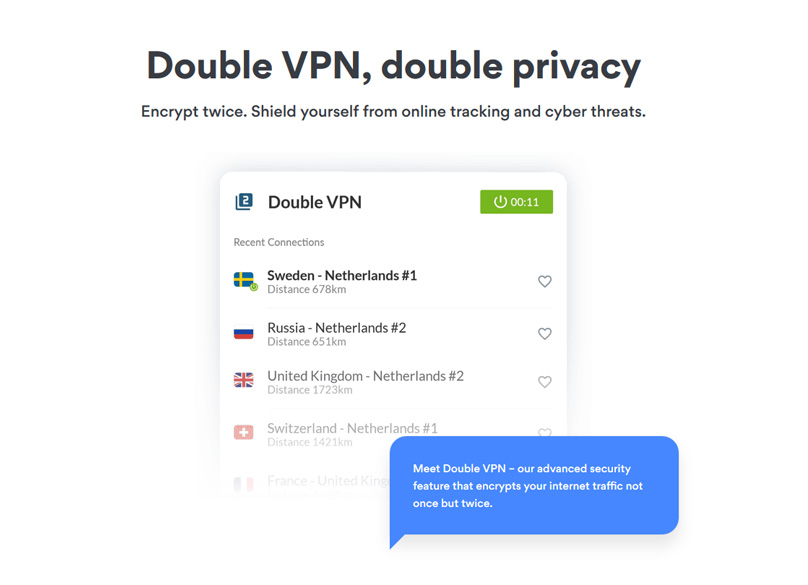
NordVPN highlights that Double VPN is particularly beneficial for groups such as political activists, journalists, individuals evading government scrutiny, and those shielding their sources.
For regular private browsing, using a Double VPN is typically unnecessary, as a standard VPN suffices. Double VPNs may also reduce connection speed, making them less ideal for tasks requiring swift internet connections. It's also redundant for Tor Browser usage, as NordVPN offers another feature specifically for that purpose.
Double VPN comes included with every NordVPN subscription. It’s accessible for platforms like Windows, Android, and macOS using OpenVPN. You have the flexibility to enable or disable it based on your preference.
What Is Onion Over VPN?
Exclusive to NordVPN is the Onion Over VPN feature, which boosts security by combining the Onion Router (Tor) with a VPN tunnel. This nifty feature enables connection through the Onion network with just one click, or you can simply connect to NordVPN as usual when using Tor.
Employing Onion Over VPN boosts your anonymity against surveillance from authorities or your ISP. While your ISP might usually detect Onion usage, NordVPN conceals this entirely. Plus, with VPN tunnel encryption, your data receives added protection.
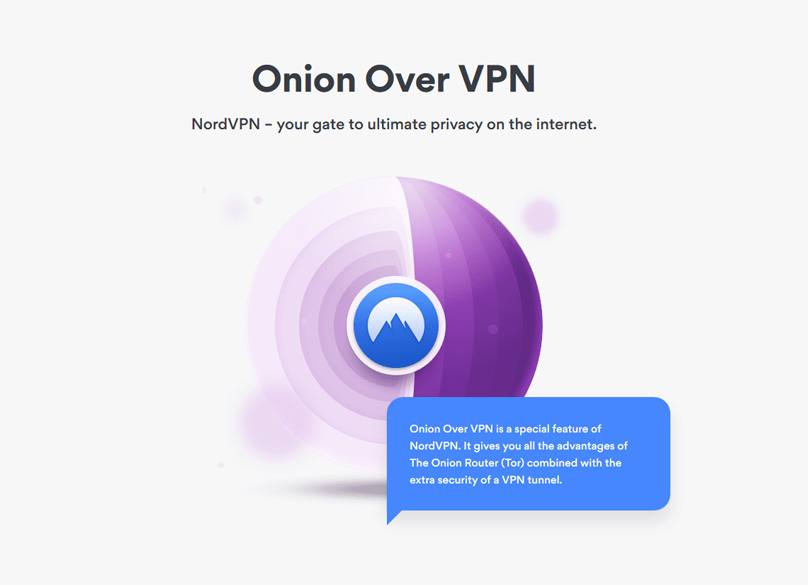
Onion Over VPN extends multiple anonymity layers. You initially access the Onion network through a random entry point, progressing through various servers, enveloping your data in encryption at every turn. As you exit, these layers peel away, decrypting your data through a random node, leading you to your desired internet location.
Using Onion without NordVPN allows ISPs to track your Onion usage, posing risks, especially in restrictive regimes. Additionally, as Onion servers are often volunteer-operated, there's a danger of compromised or malicious nodes genuinely tracking users. NordVPN’s Onion Over VPN dismisses this risk entirely.
NordVPN suggests the Onion Over VPN feature serves journalists and political activists well. It’s particularly advantageous in regimes with heavy government monitoring and logging of internet traffic—not to mention for those handling sensitive or confidential information.
NordVPN’s High-Security Encryption
A major appeal of NordVPN is its military-grade encryption, safeguarding your communications from cybercriminals, ISPs, or even government entities. Without such encryption, data passes openly through ISPs, who can easily save, share, or use it—possibly even providing it to third parties or selling it to advertisers.
Choosing a VPN with military-grade encryption like NordVPN limits your ISP’s resourcefulness, ensuring that all web traffic flows through an encrypted VPN tunnel. This process not only encrypts but also conceals your location and IP address.
With NordVPN, your data receives strong encryption via the construction of a secure VPN tunnel. Data sent online is broken into packets, with private data encapsulated and conveyed through the VPN tunnel. On arrival at VPN servers, the outer packets are removed and decrypted, rendering intercepted data unreadable by unauthorized parties.
NordVPN employs AES encryption with 256-bit keys for a military-grade security standard. This level of security is endorsed by NASA for safeguarding classified and top-secret information. With a 256-bit key, the combination count is astronomical, requiring yet-to-exist supercomputers for decryption.
How Does NordVPN Offer Protection from DNS Leaks?
NordVPN incorporates DNS leak protection technology to maintain privacy and secure technology. If DNS servers dispatch unencrypted queries outside the VPN tunnel, DNS leaks occur. Remember, DNS translates domain names to IP addresses for connectivity.
DNS leaks signify unencrypted DNS requests veering outside the VPN tunnel. These leaks particularly occur with manual VPN setup or insufficient protection. NordVPN’s DNS leak protection obstructs ISPs from discovering traces of your online activity.
Unpacking NordVPN’s Automatic Kill Switch
The Auto Kill Switch fruitions as another NordVPN security measure. It functions as an advanced security layer, ceasing data exposure online. This feature vigilantly confirms your VPN server connection, and any interruptions lead to temporary web access blocks.
In essence, the Kill Switch operates as a conclusive defense line if connectivity with NordVPN falters, averting the exposure of your IP and personal data. Upon VPN tunnel restoration, internet access resumes seamlessly, thanks to the Kill Switch, although you may opt to deactivate it.
NordVPN’s Kill Switch varies based on your device. On Windows or macOS, you may completely block internet access short of a server drop, or restrict it to selected applications, favoring app-specific blocking for advanced users.
On NordVPN’s iOS platform, the Kill Switch secures the entire network during VPN disconnection. Android 7+ users can engage the Kill Switch via native settings under wireless, networks, and VPN.
Is Employing the Kill Switch Essential With NordVPN?
NordVPN boasts numerous server availability for reliability, but connectivity issues can arise from distinct elements. More frequently, interruptions stem from unstable internet providers, notably with frequent disconnections or timeouts.
Potentially, antivirus software or firewalls could obstruct NordVPN from establishing VPN tunnels, activating the Kill Switch until exceptions alleviate this. Automatic updates potentially trigger reboots sans VPN protection. Though improbable, NordVPN might face disruptions; for example, a single incident involved third-party cable damage during construction. At that moment, the Kill Switch demonstrated its value.
For optimal privacy, NordVPN advises keeping the Kill Switch activated, particularly in countries with strict governmental oversight, for political activists, journalists, and those handling confidential tasks. Ensure prior activation of the Kill Switch before communicating sensitive information, such as passwords.
What VPN Protocol Does NordVPN Use?
NordVPN utilizes two distinct VPN protocols for initiating VPN tunnels. The IKEv2 (Internet Key Exchange) collaborates with IPsec (Internet Protocol Security) to deliver enhanced speed, security, and stability, resisting supercomputer breaches using advanced cryptographic keys and algorithms. NordVPN embraces Next Generation Encryption (NGE), with IKEv2/IPsec known for adaptability amid cryptographic developments.
OpenVPN serves as the alternative protocol, adaptable for security, leveraging UDP and TCP ports. This versatility accommodates safe browsing, live streaming, and gaming. NordVPN employs AES-256-GCM encryption alongside a 2048-bit DH key for safeguarding sensitive data, with OpenVPN’s open-source code assuring quality.
IKEv2/IPsec stands as the default NordVPN protocol for macOS and iOS platforms, whereas OpenVPN prevails on Android, macOS, and Windows applications.
NordVPN Speed
Advocating both speed and security, NordVPN prevents typical VPN-induced browsing slowdowns via ultra-fast servers, ensuring negligible speed reduction. However, speed differences become more apparent during streaming and file sharing, where NordVPN’s rapid servers prove invaluable.
NordVPN enhances internet velocity by bypassing ISP throttling, ensuring swift, secure streaming devoid of slowdowns, even on public Wi-Fi. The speedy service ensures reliable security concurrently.
Several factors determine VPN connection speed, including encryption standards and baseline internet speed. Other variables encompass the VPN server’s proximity and load, alongside your firewall configuration and security protocol. antivirus When your internet traffic hits the remote VPN server, the encryption remains intact. It gets passed to another server, adding an extra layer of protection. With Double VPN, your data receives twice the encryption, making it much more challenging for cybercriminals to intercept.
Double VPN upgrades security by blending TCP and UDP protocols, enhancing connection safety. The second server holds no data on you as the first server alters your IP address. This technique guarantees complete privacy, as observers only see you're using a VPN, without knowing your actual online destination.
NordVPN's Streaming Capabilities: What’s SmartPlay All About?
NordVPN highlights particular groups who may benefit from Double VPN, such as political activists, journalists, and individuals keen on evading state surveillance, or those in need of source protection.
Double VPN isn't a necessity for everyday safe browsing; a standard VPN suffices for that. Using Double VPN might reduce connection speed, which isn't ideal when high speed is vital. There's no need for it with Tor browsing since NordVPN offers a separate Tor feature.
Double VPN comes included with every NordVPN subscription and is compatible with Windows, Android, and macOS via OpenVPN. You can switch it on or off whenever you like.
Onion Over VPN, a unique offering from NordVPN, adds a layer of VPN security to the Tor (The Onion Router) network. The process is a breeze: a single click routes you through the Onion network. Alternatively, just connect to NordVPN when using your Tor browser.
Using Onion Over VPN keeps you out of sight from authorities and your ISP. Normally, your ISP can tell you're using Onion, but can't observe your actions. With NordVPN, the ISP can't even detect your Onion usage, plus you get additional security from NordVPN’s encrypted tunnel.
Is NordVPN Good for P2P Sharing?
With Onion Over VPN, you gain multiple layers of anonymity by starting your connection via a random Onion entry point. As you navigate through numerous servers, your data gets encapsulated in encryption, which is removed layer by layer. At exit, data is decrypted before emerging through a random node onto the internet.

Without NordVPN, if you use Onion, your ISP will know you're using it, which carries risks, especially in heavily censored countries. There's also the vulnerability that Onion servers are volunteer-run, meaning potentially compromised servers could track you. NordVPN eliminates this risk with Onion Over VPN.
NordVPN recommends Onion Over VPN for those such as journalists and political activists. It's invaluable for those living under regimes where government monitors and logs internet activity, or anyone handling sensitive information.
NordVPN Device Support & Apps
A standout feature of NordVPN is its use of military-grade encryption, keeping your data safe from hackers, ISPs, and government eyes. Without such encryption, traffic passes through your ISP, enabling them to read and potentially share or sell your data, or provide it to authorities.
Military-grade encryption prevents your ISP from accessing your internet activity. Traffic is funneled through a secure VPN tunnel, which not only encrypts your data but also conceals your geographical location and IP address.
NordVPN employs military-level encryption by creating a safe passage for your data. Data is segmented into packets, which NordVPN then securely encapsulates, sending them through a VPN tunnel. At the VPN server endpoint, the packets are deconstructed, and data decrypted ensuring that interception yields nothing to decipher.
NordVPN’s military-grade choice, specifically the AES with 256-bit keys, aligns with NASA's standard for protecting classified data, including TOP SECRET. With a 256-bit key, there are an astronomical 1.1×1077 possible combinations, requiring future-tech-level supercomputers to crack.
NordVPN utilizes DNS leak protection technology to safeguard your online privacy and data. This protection is vital if DNS queries, essential in translating URLs into IP addresses, remain outside the VPN's secure tunnel.
How Do You Use NordVPN?
A DNS leak, where DNS requests bypass the VPN tunnel, results in unencrypted data exposure. Such leaks are possible with manual VPN setups or without adequate protections. NordVPN boosts your privacy by keeping DNS requests within the tunnel, shielding them from ISP scrutiny.
NordVPN offers an automatic Kill Switch, enhancing your security by preventing accidental data exposure online. This feature vigilantly watches for a VPN server connection, cutting your device's internet access if the connection fails.
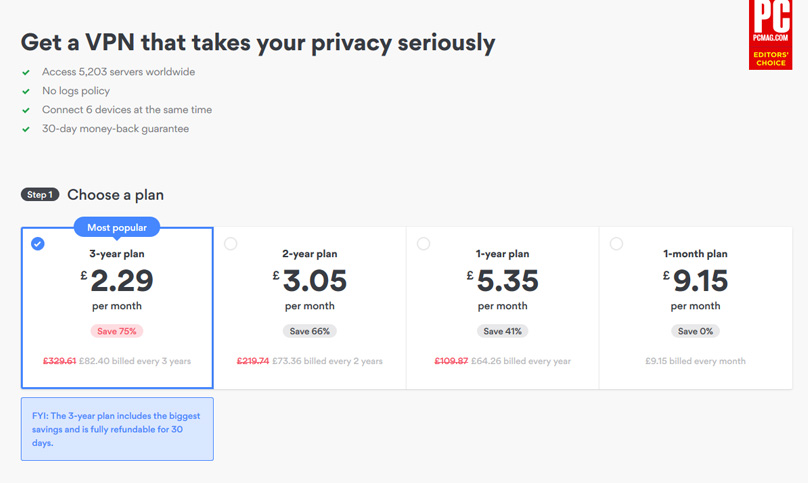
What Plans Does NordVPN Offer?
Acting as a safety net, the Kill Switch kicks in if your NordVPN connection drops, preventing your real IP and data from being exposed. When the VPN reconnects, internet access restores automatically, though you can turn the Kill Switch off if desired.
Depending on the device, NordVPN offers variations of the Kill Switch. On Windows and macOS, you can opt to halt all Internet activity in case of a server drop or restrict certain apps. The former offers maximum safety, while the latter is for more advanced users.
On iOS devices, NordVPN’s Kill Switch secures network access whenever the VPN connection drops. Android users (version 7 and up) can activate it in the native settings under wireless and network options.
Although NordVPN boasts numerous servers, connection issues can arise due to various factors. More often than not, unstable internet, not NordVPN itself, causes disconnections, especially if your network frequently disconnects.
Is There a Free Trial From NordVPN?
Your antivirus or firewall could inadvertently block NordVPN, preventing tunnel creation. Until rectified via exception list additions, the Kill Switch remains active. Automatic updates may necessitate a reboot without VPN, and though rare, NordVPN might suffer issues; a third-party incident once led to cable damage, highlighting the Kill Switch's utility.
NordVPN Payment Options
NordVPN advises keeping the Kill Switch on when privacy matters most. Activists or journalists, especially in repressive regions, should always have it engaged. It's equally essential for those handling sensitive work data and advisable when entering any privacy-compromising information.
NordVPN Affiliate Program
NordVPN leverages two protocols in shaping the VPN tunnel. The first, IKEv2 combined with IPsec, offers speed, stability, and robust security using nearly unbreakable cryptographic keys; its Next Generation Encryption (NGE) adapts as cryptographic advancements emerge.
OpenVPN, the alternative protocol, operates on versatile UDP and TCP ports, making it ideal for streaming, gaming, and secure browsing. It safeguards sensitive data using AES-256-GCM with a 2048-bit DH key. Open source in nature, OpenVPN is continuously scrutinized for quality assurance.
NordVPN Customer Support
On macOS and iOS NordVPN apps, IKEv2/IPsec is the standard protocol, whereas Android and Windows utilize OpenVPN by default.
While robust security can slow VPN browsing speeds due to extra routing steps, NordVPN alleviates this via ultra-fast servers, minimizing noticeable speed differences aside from when streaming or file sharing. In such scenarios, these servers shine.
NordVPN not only provides fast internet through ISP throttling bypass, but also offers secure, seamless streaming. This quick service ensures a speedy, safe connection, even over public Wi-Fi.
VPN speed depends on a range of factors including encryption strength, internet velocity, server proximity, and server load. Your device type and security settings also affect it.
Other VPN Providers
Once your online traffic hits the remote server of your VPN, it remains safely encrypted. After this point, it is sent through an additional VPN server for another round of encryption. With Double VPN, your information gets safeguarded under two encryption layers, doubling the difficulty for hackers to penetrate it.
Conclusion
The Double VPN enhances overall security by using a combination of TCP and UDP protocols. Notably, the secondary server can't uncover any details about you, as your initial IP address was masked by the primary VPN server. This guarantees unmitigated privacy because nobody can trace your exact web destination, though they will recognize your VPN usage.
NordVPN suggests that certain groups might benefit significantly from the Double VPN feature, such as journalists, political activists, and those looking to dodge government watchfulness or protect sensitive sources.
For everyday private browsing, a standard VPN should suffice, making a Double VPN overkill and potentially slowing your connection, which is impractical if speed is essential. There's also no need to utilize Double VPN with Tor browsing due to NordVPN’s separate features designed for that purpose.
Double VPN capabilities come packaged in any NordVPN subscription, available for Windows, Android, and macOS users via OpenVPN. You have the flexibility to enable or disable it whenever you prefer.
NordVPN
Pros
- Great Security & Privacy
- Onion Over VPN is an exclusive feature found in NordVPN, which combines the Tor network's strengths with added security from a VPN tunnel. This feature is very streamlined; with just a click, you are routed through the Onion network. Alternatively, you can connect to NordVPN and then use your Tor browser as usual.
- Lots of Servers & Locations
- Good Pricing
- Excellent Reputation
Cons
- No Phone Support
- No Free Trial






2Comments
I asked NordVPN:
Adopting a VPN that utilizes military-grade encryption prohibits your ISP from accessing your online activities. All your traffic traverses a secured encrypted tunnel, not only safeguarding your data but also obscuring your location and IP address.
NordVPN accomplishes encryption through the creation of a VPN tunnel. Information sent over the internet is compartmentalized into packets. NordVPN takes these packets, encloses them, and sends them through the secure VPN tunnel. On reaching VPN servers, the outer packet is stripped away, and data is decrypted, thus making it unreadable even if intercepted.
NordVPN 6.25 (latest)
NordVPN 6.24
https://nordvpn.com/blog/nordvpn-windows-release-notes/
NordVPN’s answer:
Thank you for your letter.
NordVPN employs AES encryption with 256-bit keys—a standard which even NASA endorses for highly classified TOP SECRET data. The strength of this encryption lies in its millions of potential combinations, making it impenetrable for supercomputers not yet in existence.
NordVPN utilizes technology to guard against DNS leaks. This preventive measure is particularly vital as DNS servers might send inquiries that remain unencrypted, outside the protective VPN tunnel. DNS, which stands for Domain Name System, converts domain names into IP addresses.
A DNS leak may occur if VPN-related settings are improper, exposing unencrypted DNS requests. By mitigating DNS leaks, NordVPN helps ensure your ISP cannot unearth snippets of your online footprint.
Best Regards,
Customer Success Team
A key security facet of NordVPN's services is the automatic Kill Switch. This sophisticated feature blocks any possibility of data leaking online. It monitors the VPN connection’s status diligently and temporarily halts internet access if your connection ceases.