Consensus frameworks serve as the cornerstone of distributed blockchain networks, playing a pivotal role in their operation. These models create a foundation that enables users to engage without trust, transforming cryptocurrency platforms into innovative networks with remarkable capabilities.
In the landscape of distributed networks, Byzantine Fault Tolerance this refers to a network's resilience whereby it can continue to operate correctly and reach necessary consensus even in the face of faulty or deceitful nodes that may spread false information.
The goal is to protect the network from disastrous failure by minimizing the control that malicious nodes can exert, ensuring that honest nodes reach the correct consensus.
Derived from the Byzantine Generals’ Problem This challenge has undergone extensive study and refinement with various solutions already in implementation and new ones continually being developed.
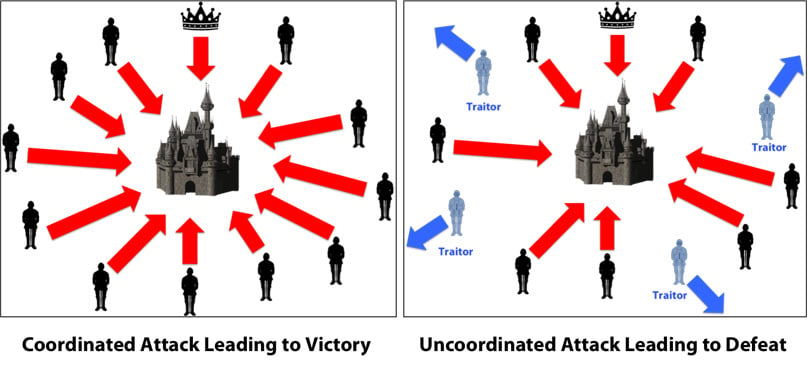
Visualizing the Byzantine Generals’ ProblemDebraj Ghosh
Practical Byzantine Fault Tolerance, or pBFT, stands as one such refinement. It was introduced by Miguel Castro and Barbara Liskov through a groundbreaking paper in 1999 entitled Exploring Practical Byzantine Fault Tolerance .”
Its purpose is to enhance traditional BFT consensus methods and has since been adopted and improved across numerous modern distributed computer networks, including some widely recognized blockchain systems. platforms .
In Short: Practical Byzantine Fault Tolerance is a mechanism that ensures distributed systems, like blockchains, can securely agree on state and transactions despite the presence of malicious nodes.
Key Facts
| Key Facts | Description |
|---|---|
| Consensus Models | An essential element for the smooth functioning of distributed blockchain systems, paving the way for interactions devoid of the need for trust. |
| Byzantine Fault Tolerance (BFT) | The strength of a network in reaching consensus even when facing unreliable or potentially harmful nodes. |
| Delving into Practical Byzantine Fault Tolerance | An advancement of BFT brought forward by Miguel Castro and Barbara Liskov in 1999, now embedded in advanced systems to elevate both safety and performance. |
| pBFT Algorithm | Operates under the assumption that fewer than a third of the nodes exhibit malicious behavior. It guarantees both continuity and protection, maintaining linearizability, meaning all client requests deliver valid responses. |
| pBFT Node Structure | Features one main distributor (lead node) and several supporting nodes, with leadership rotating in a predictable order. |
| pBFT Communication and Phases | It involves intensive communication exchange between nodes across four stages: the client's request to the lead, transmission to backup nodes, request execution, and response, then the client waits forf+1 matching replies. |
| Transaction Certainty and Lower Energy Demands | The pBFT grants immediate certainty of transaction outcomes while consuming significantly less energy compared to models like Proof-of-Work, thus reducing overall energy demands. |
| Limitations | Ideal for smaller groups achieving consensus due to the significant communication burden. The efficiency and scalability of the algorithm diminish as the network grows larger. |
| Message Authentication | Employs digital signatures and multisignatures, foregoing MACs, for efficient and verifiable authentication among large groups, addressing original limitations of pBFT. |
| Susceptibility to Attacks | Prone to Sybil attacks, though this risk lessens with larger confirmations. The ongoing task is to retain robust security while improving communicative scalability. |
| Modern Implementations | Blockchain solutions such as Zilliqa integrate optimized pBFT for enhanced throughput, partnering with PoW for extra security. Hyperledger Fabric incorporates a tailored pBFT version, thriving with smaller, specific consensus groups for efficient transaction handling. |
| Importance for Cryptocurrencies | Sophisticated BFT protocols stand as pillars for the reliability and trust-free essence of expansive public blockchains, with pBFT serving as a foundational component for numerous extant cryptocurrencies. |
A Closer Look at Practical Byzantine Fault Tolerance
The pBFT scheme targets offering a practical replication mechanism that accommodates Byzantine faults (malicious nodes), assuming node malfunctions and misinformation spread by distinct nodes.
Crafted to function within asynchronous settings, the algorithm is streamlined to maintain high efficiency with modest latency increments.
- Fundamentally, nodes within a pBFT system align in sequence, highlighted by one acting as the primary node (leader) and others fulfilling backup roles.
- Every node communicates extensively with its peers, aiming to achieve consensus amongst honest nodes through majority agreement regarding system status.
- Nodes partake in rigorous dialogue, obligating them to authenticate message origins and ascertain their unaltered state during transfer.
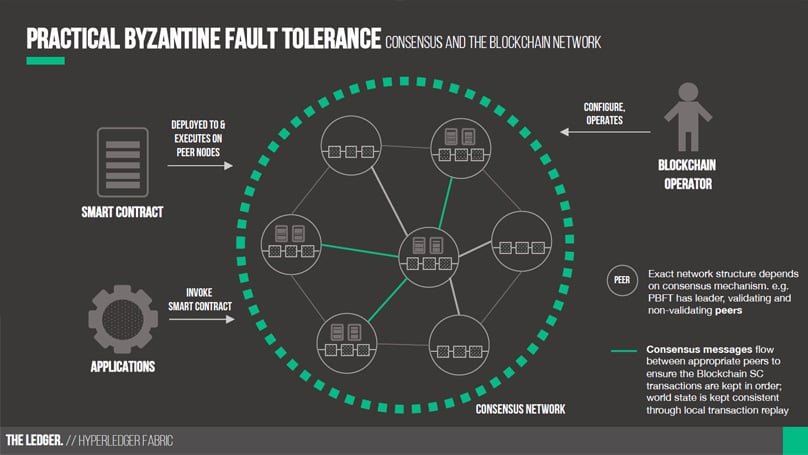
Evoking Practical Byzantine Fault Tolerance through Images Altoros
For the effectiveness of a pBFT system, it's essential that malicious nodes do not comprise a third or more of the network within a certain vulnerability period.
As the node count rises, the chance decreases for malicious nodes nearing or surpassing this threshold, ensuring the system remains both live and secure provided at most 1/3 cannot fail at once.
Ultimately, client-acquired replies correctly mirror their demands because of linearizability .
Each iteration of pBFT consensus, identified as views, divides into four distinct segments that resemble a 'Commander and Lieutenant' framework rather than the equal-status nature of the Byzantine Generals' quandary, attributed to a standout leader node. The segments are as follows.
- A client issues a request to the leader node to execute a desired service function.
- The leader node relays the request to the backup nodes.
- Nodes carry out the request and deliver their responses back to the client.
- The client anticipates receiving f + 1 confirmations (f designates the maximum faulty nodes) reflecting uniform outcomes across various nodes.
Nodes must uphold determinism, initiating from a common state, which culminates in unanimous agreement by honest nodes concerning the order of recorded data, leading to either its acceptance or rejection.
The leader role cyclically rotates each cycle and can be swapped via a 'view change' protocol if unresponsive past a given time.
A formidable majority of honest nodes may determine a leader's unreliability, ejecting them in favor of the subsequent candidate.
Pros and Cons of the pBFT Approach
The pBFT consensus construct was aimed at practical applications, with noted limitations alongside strategies to incorporate it efficiently in real-world systems.
Conversely, the pBFT presents distinct benefits when measured against other consensus schemas.
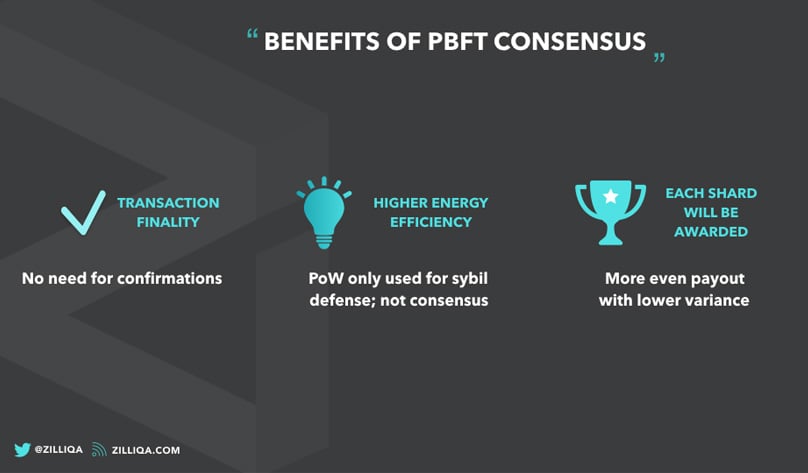
Benefits of pBFT, Image by Zilliqa
A standout benefit of the pBFT model is delivering transaction certainty without extra confirmations, unlike systems like Bitcoin's PoW.
Once nodes within a pBFT setup reach agreement over a block, that block's status is definitive, validated by the unanimous node consensus over system status specifically at the time through mutual communication.
Beyond finality, the pBFT model's energy savings create another edge over PoW systems. markedly diminished energy consumption .
In a Proof-of-Work model such as in Bitcoin , each PoW cycle coincides with a block, translating into the substantial yearly electricity requirement rivaling entire small nations. Bitcoin network by miners Given pBFT's minimal computational toll, it naturally leads to lowered electricity use as miners circumvent solving PoW's resource-heavy hashing tasks.

While offering straightforward advantages, the pBFT consensus framework does encounter significant drawbacks. Principally, it functions best within smaller consensus groups in its traditional capacity due to the extensive node communication needed.
Despite mentions of using digital signatures and MACs (Message Authentication Codes) as verification formats, MACs fall short for extensive node communication in sizable consensus groups like crypto networks. Furthermore, MACs struggle to convince third-party message authentications.
Even though digital signatures and multisigs significantly upgrade over MACs, counteracting the pBFT model's communication constraint while securing its safety is an essential hurdle for any implementation endeavor.
where a single entity can forge or alter numerous identities (network nodes), posing a network risk.
Модель pBFT также подвержена Сибил атакам This threat eases within larger networks, although pBFT model scalability and throughput capabilities decrease with size, needing optimization or hybrid consensus model integration.
At present, various blockchain platforms deploy either optimized or mixed pBFT versions as consensus strategies or components, frequently alongside alternative consensus mechanisms.
Contemporary Platforms Utilizing Enhanced pBFT Models
Exploring the Basics of Practical Byzantine Fault Tolerance
Zilliqa
Zilliqa employs a highly optimized version of classical pBFT in combination with a PoW consensus round every 100 blocks. They use multisignatures to reduce the communication overhead of classical pBFT and in their own testing environments, they have reached a TPS of a few thousand with hopes to scale to even moreas more nodes are added.
Byzantine Fault Tolerance is a thoroughly examined idea in the realm of distributed systems. Its presence in contemporary infrastructures plays a pivotal role in supporting the operation of cryptocurrencies today.
Hyperledger
Hyperledger Fabric Understanding Practical Byzantine Fault Tolerance: A Beginner’s Guide
A Deep Dive into Practical Byzantine Fault Tolerance
Consensus mechanisms are the cornerstone of decentralized blockchain ecosystems. They are crucial for ensuring that participants can engage with each other seamlessly and confidently, without the need for third-party mediation. When embedded accurately into cryptocurrency architectures, they pave the way for groundbreaking networks with incredible opportunities.
Заключение
In distributed computing environments,
it's crucial that the network continues to operate correctly and reaches agreement on new transactions, even if some parts of the system behave wrongly or spread incorrect data.







9Комментарии
systems, including several prominent blockchain
n минус ⅓ ?????
(n-1)/3
Key Takeaway: Practical Byzantine Fault Tolerance is an innovative approach allowing blockchain networks to confirm transaction authenticity robustly, despite potentially malicious nodes, through rigorous communication protocols that affirm system integrity.
n-1
___
3
An In-depth Look at Practical Byzantine Fault Tolerance
Weighing the Pros and Cons of the pBFT Framework
Это 3f+1 (чтобы удовлетворить правило 2/3)?
No, they only need to wait for f + 1.
Contemporary Platforms Harnessing Upgraded pBFT Technologies
Essential to blockchain viability, fostering decentralized user interactions devoid of trust constraints.
A network’s resilience in achieving consensus when faced with nodes that may falter or execute harmful actions.
Practical Byzantine Fault Tolerance (pBFT)
Introduced as an enhanced version of Byzantine Fault Tolerance by Miguel Castro and Barbara Liskov in 1999, this approach serves to reinforce performance and security in modern environments.
Please explain.
Great article by the way!
Operating under the provision that malicious nodes form less than a third of the total, it ensures stability and correctness, facilitating correct responses to client inquiries.
It features a head node and several subsidiary nodes, with leadership rotating systematically.
Communication between nodes is intensive and involves several steps: a client's request to the primary node, distributing it to others, performing the operations, and relaying the outcome.
End Results and Energy Use Efficiency
Through pBFT, transactions are confirmed immediately and consume less energy compared to Proof-of-Work methods, which helps decrease the overall energy requirements of the network.
Best fit for small consensus setups, due to the extensive communication required. As the network size grows, the benefits of scalability and throughput lessen.
Adopts digital and multisignatures over traditional Auth Codes for better efficiency in larger setups, tackling initial pBFT limitations.